It starts with a leaky faucet.
A resident texts a photo directly to your maintenance tech. It’s after hours. The tech responds:
“Can you FaceTime me real quick? I just want to see how bad it is.”
They do. The tech takes a quick screenshot to show the manager. Problem solved—for now.
But now the resident has the tech’s personal number. And the tech has theirs. So when something else breaks, they skip the portal, the hotline, your entire ops stack—and just text each other.
Boundaries blur. Communication goes off-grid.
Then things change.
The resident moves out. The tech quits. But the thread lives on. The contact stays saved. And one day, someone sends a message:
“Hey—do you still have that screenshot from the bathroom leak?”
Or worse: the resident still has the tech’s number after they’ve left your company. Or the tech—now unemployed, maybe even disgruntled—still has access to the resident. There’s no offboarding process for personal phone numbers. The thread lives on.
Now the former resident files a complaint:
“I never gave permission to be recorded. I want a copy of that footage—and I want to know how it’s being used. I want proof it was deleted.”
And maybe the former tech feels burned too.
They’re out. They’re bitter. They remember those after-hours calls, the FaceTimes, the lack of clear policies. And now they’re asking questions.
What data did they share?
What liability are they carrying?
Who’s really responsible?
Now you’re looking at a privacy complaint. Possibly a lawsuit. Maybe two. Maybe a regulator shows up.
And while the tech made the call and the manager didn’t stop it, you—the owner—are the one who pays.
The Tech Acts. The Manager Enables. The Owner Pays.
It doesn’t matter whether you self-manage or hire a third-party firm.
If resident communication happens under your roof, and something goes wrong— you’re on the hook.
The tech? At risk of discipline or legal blowback.
The manager? Could be named in a complaint, lose a license, or get deposed.
But you—the asset owner—are the one with financial exposure.
Because the courts, the regulators, the lawyers—they follow the money.
And the money is yours.
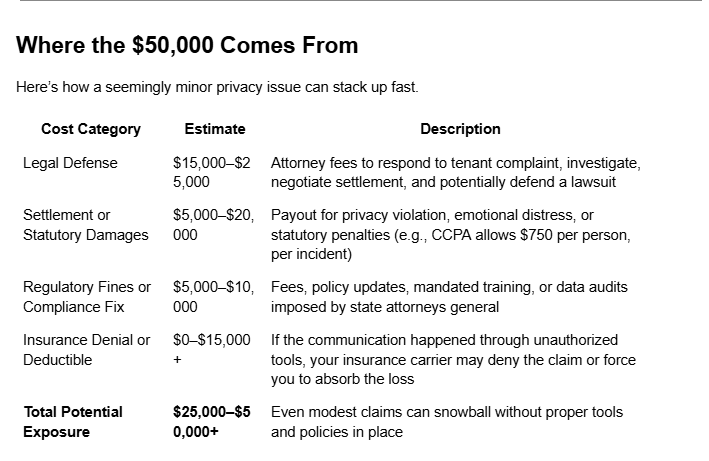
What the Law Says (and Why It Matters)
If you’re operating in California, Texas, or Florida, you’re exposed to clear, enforceable privacy regulations.
California – California Consumer Privacy Act (CCPA) / CPRA
- Tenants have the right to know how their data is collected, used, stored, and shared.
- You must provide notice at collection and allow access, deletion, and opt-out.
Texas – Texas Data Privacy and Security Act (TDPSA)
- Effective July 2024, requires “reasonable” security measures and clearly defined data usage practices.
- Mandates disclosures and restrictions on sharing sensitive data.
Florida – Digital Bill of Rights
- Restricts unauthorized data collection and mandates clear disclosure of data practices.
- Tenants must be informed when their personal information—including images or videos—is collected or used.
In these states, if a resident’s image, voice, or personal surroundings are recorded or shared without consent, you are legally responsible—even if your team was just “trying to help.”
What Owners Should Do Now
The communication gap is no longer operational—it’s a legal and financial one. Here’s how to close it:
1. Prohibit Informal Tools
- Ban FaceTime, WhatsApp, and text messaging for resident communication.
- Require all interactions to happen through company-approved systems with encryption, logging, and consent capture.
2. Require Written Consent
- Add image and video consent language to maintenance requests, lease agreements, or call scripts.
- Don’t rely on verbal “go-ahead” or assumptions.
3. Use Compliant Platforms
- Adopt tools with SOC 2 or ISO 27001 certifications, media logging, and built-in consent workflows.
- Ensure all media is automatically tied to resident records and stored securely.
4. Update Contracts and Oversight
- Require third-party managers and vendors to comply with your communication and data handling policies.
- Build in indemnification for unauthorized use of resident data.
5. Train Techs and Managers
- Train frontline staff on what’s allowed and what’s not.
- Make it clear that even helpful gestures—like “just send me a quick pic”—carry risk without proper process.
Final Word: Good Intentions Don’t Protect You
Your tech may mean well. Your manager may look the other way. But when things go sideways?
You’re the one who pays.
Courts and regulators don’t want to hear about convenience. They want to see:
- A documented communication policy
- Evidence that consent was captured
- Proof that secure, compliant tools were used
If you can’t provide that, you’re writing the check.
Protect the asset. Protect your balance sheet. Lock down your communication protocols—before the $50 fix becomes a $50,000 problem.




